In an age where digital transactions are rapidly becoming the norm, the importance of cybersecurity cannot be overstated. Isn’t it alarming how something as innocuous-sounding as “spyware” can spell disaster for our personal and financial security? Unilever.edu.vn is here to delve deep into what spyware is, how it operates, and its particular dangers in the world of cryptocurrencies.
What is Spyware?
Spyware, often referred to as malicious software (malware), operates stealthily in the background of your devices, meticulously monitoring and recording user activities to collect sensitive information. Typically, this data harvests personal details and can be sent back to cybercriminals for various nefarious purposes, including identity theft, sales of stolen data, or even industrial espionage.
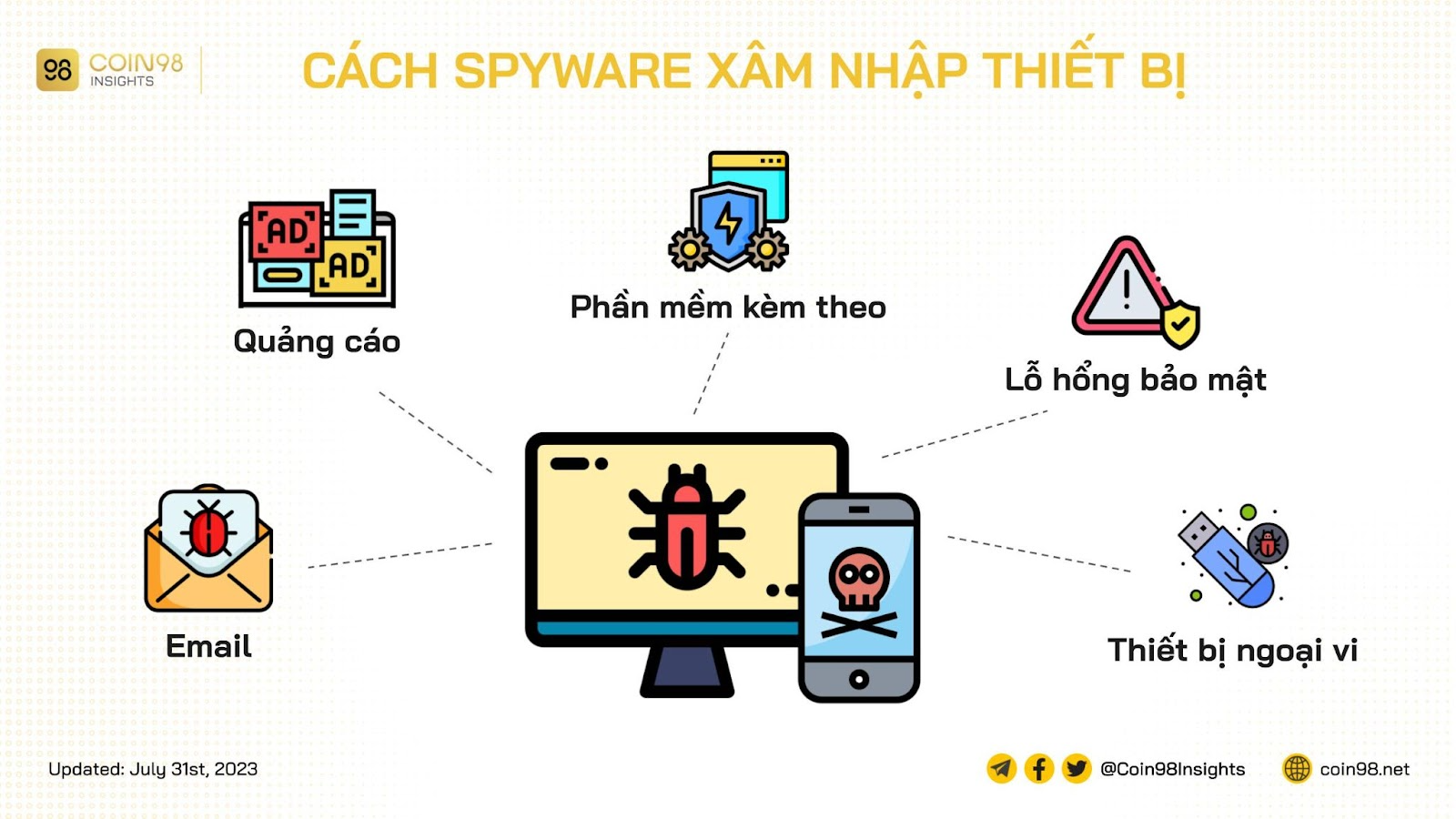
Image of spyware systems monitoring
How Do Spyware Attacks Occur?
Spyware has numerous ways to infiltrate systems—whether through computers, smartphones, or tablets—making it imperative to understand the various vectors of attack. Devices running on Windows, unfortunately, tend to be more susceptible due to their relatively weaker security systems. However, even Apple devices are not immune, as hackers continually devise more sophisticated attacking strategies.
Common Methods of Spyware Infection
Bundled Software: Sometimes, spyware is stealthily integrated into seemingly harmless software, such as file cleaners or web browsers. Users may unknowingly install spyware while attempting to get legitimate software.
Phishing Emails: Cybercriminals may use deceptive emails containing suspicious attachments or links. If users click these links or open attachments, they can unwittingly allow spyware to enter their devices.
Malicious Ads: Clicking on ads from unknown websites can also lead to spyware infections, as these ads may harbor infected code.
Security Flaws: Hackers often exploit vulnerabilities in software code or hardware to install spyware without permission.
Infected USB Drives: External devices can also carry spyware. Connecting an infected USB device could compromise the user’s system.
Types of Spyware in the Crypto Space
System Monitor Spyware
This type of spyware, known as InfoStealer, primarily focuses on collecting sensitive personal information, such as credentials and financial information. Examples include:
- Keyloggers: Record keystrokes made by the user.
- Screenloggers: Capture screenshots of user activity.
- Clipboard Monitors: Track clipboard contents, replacing copied information to redirect transactions to criminal addresses.
- Memory Scrapers: Seek out sensitive data stored in your device’s memory.
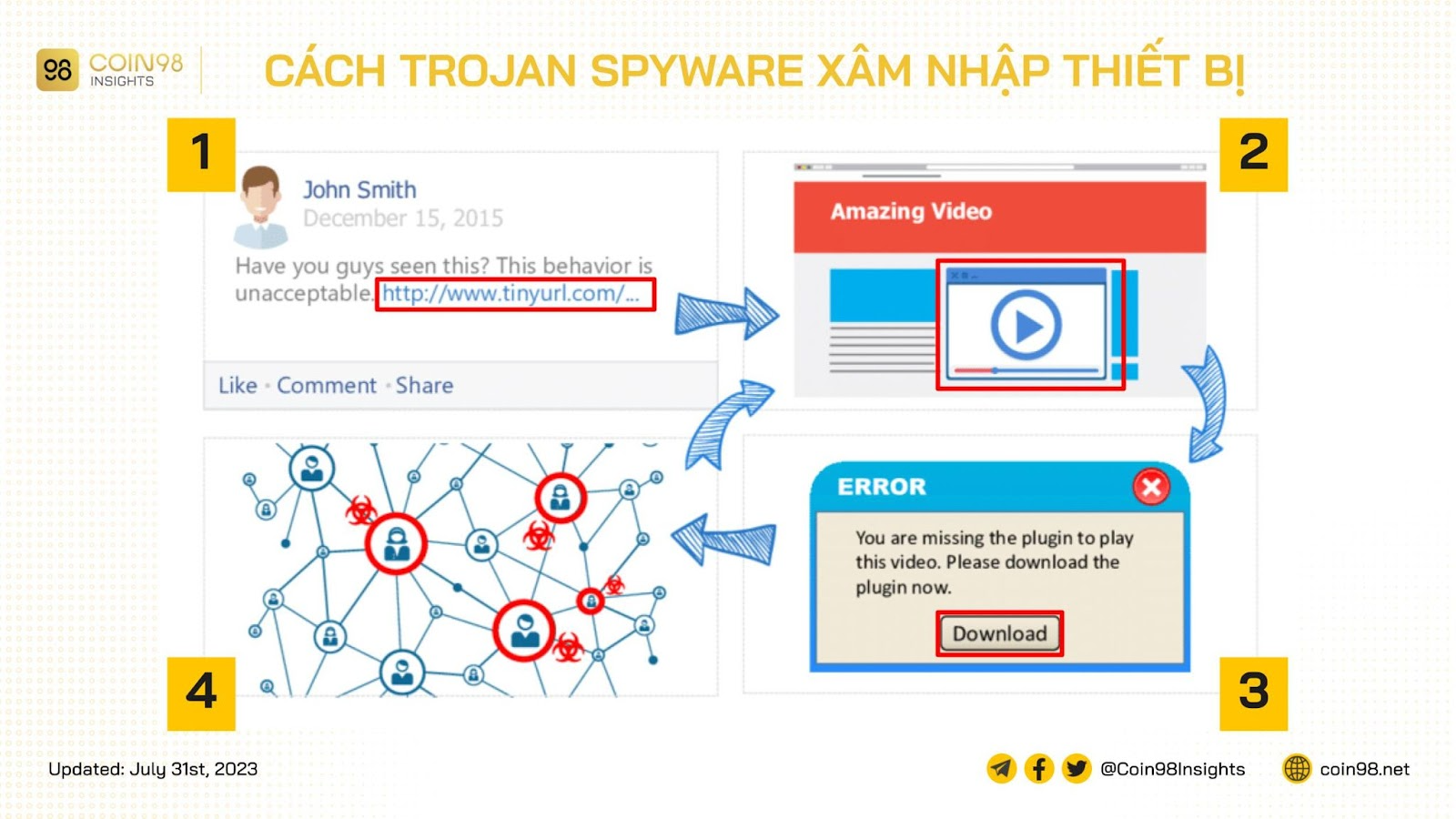
Trojan Spyware
Trojan spyware masquerades as legitimate software, tricking unsuspecting users into downloading harmful programs disguised among files, movies, or games. A successful Trojan can do significant damage, including:
- Corrupting data.
- Hijacking user control.
- Disabling security features.
- Extracting sensitive information, including cryptocurrency keys.
Botnet Spyware
This type refers to a network of infected devices that are controlled remotely by hackers, allowing for large-scale cyberattacks. Botnets can execute:
- Distributed Denial of Service (DDoS) attacks.
- Large-scale fraud efforts based on collected user data.
- Sale of sensitive information on the dark web.
Common spyware applications on mobile devices
The Dangers of Spyware in Crypto
As cryptocurrencies gain popularity, the threats posed by spyware also escalate. The stakes are particularly high because:
- Private Key Compromise: Spyware can acquire private keys and allow hackers to seize control of digital assets.
- Transaction Monitoring: Cybercriminals can observe users’ transactions, breaching their privacy.
- Facilitation of Other Malware Attacks: Spyware may open doors for further malware attacks.
- Identity Theft: Personal information collected can lead to fraudulent activities, making it crucial to safeguard your data.
Notable Incidents
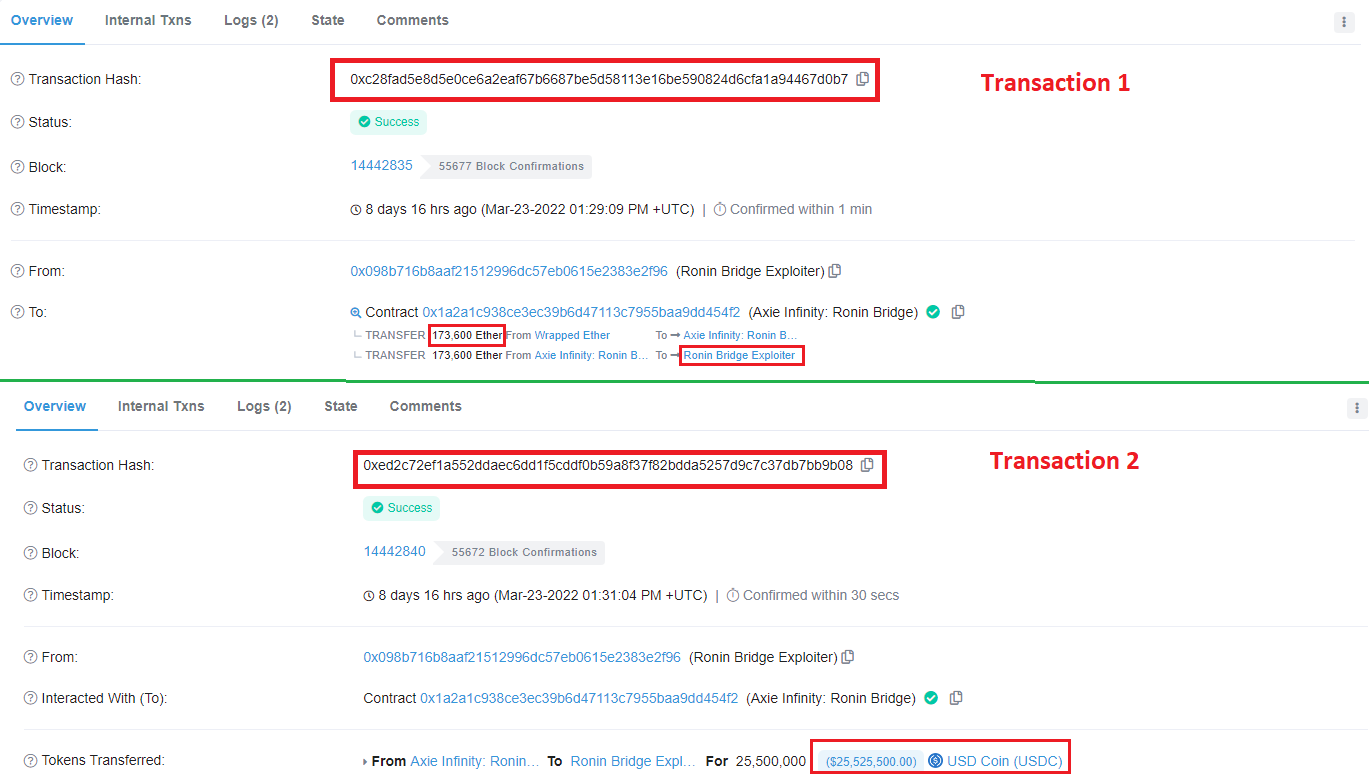
One of the most infamous incidents highlighting the hazards of spyware occurred during the Ronin Network hack, where attackers initially gathered intelligence on Sky Mavis employees. They lured an unsuspecting engineer with a fake job offer, delivering an infected PDF. Upon download, spyware infiltrated the entire network, resulting in astounding losses of over $600 million. This incident exemplifies the profound dangers associated with spyware in the cryptocurrency sector.
Recognizing Signs of Spyware Infection
To safeguard against spyware, stay vigilant for the following warning signs:
- Noticeable slowdown in device performance.
- Rapid battery depletion and device overheating.
- Unusual sounds during calls.
- CD drives opening spontaneously.
- Pop-up ads during browsing sessions.
- Strange alterations to your browsing history or settings.
How to Protect Against Spyware
With the crypto market’s vulnerabilities, protective measures against spyware are more critical than ever. Here are some practical tips:
Enable Firewalls: Firewalls serve as a barrier against unauthorized access attempts.
Install Antivirus Software: Use reliable antivirus tools like Bitdefender or Malwarebytes to detect and neutralize potential threats.
Implement Two-Factor Authentication (2FA): This adds an additional layer of security to your accounts, making unauthorized access more challenging.
Power Down Devices: Shut down your computer when not in use, avoiding idle time that increases vulnerability.
Keep Software Updated: Install regular updates to your operating systems and applications to patch emerging security holes.
Verify URLs: Before accessing cryptocurrency platforms, ensure you are on the official site and not redirected to a phony page.
Exercise Caution with Downloads: Only download software from reputable sources and be wary of unsolicited email links.
Conclusion
As the digital landscape evolves, so do the threats we face, particularly concerning spyware within the cryptocurrency domain. At Unilever.edu.vn, we stress the importance of maintaining a proactive stance regarding cybersecurity. By understanding spyware, recognizing its dangers, and implementing protective measures, you can safeguard your information and assets in the ever-evolving world of cryptocurrency. In this fast-paced digital world, staying informed is your best defense.
By integrating these measures and remaining alert, crypto users can navigate the landscape safely and securely. Your vigilance could potentially save significant losses from spyware attacks.