The cryptocurrency landscape is constantly evolving, with new technologies and innovations emerging at a rapid pace. Understanding these trends is crucial for both developers and users to navigate this dynamic space effectively. This article explores some of the most prominent crypto wallet technologies that are poised to define the future of digital asset management in 2025 and beyond, focusing on enhancing security, accessibility, and user experience.
NFC: Streamlining Crypto Transactions
Near Field Communication (NFC) is revolutionizing how users interact with their crypto wallets. This wireless technology allows devices to communicate with each other over short distances, enabling seamless and secure transactions without the need for physical connections or complex configurations. NFC-enabled hardware wallets, often in the form of cards, provide a convenient and portable solution for storing private keys offline, enhancing security against online threats.
 NFC technology for crypto walletsNFC technology allows users to scan their devices to sign transactions, simplifying the process and enhancing security.
NFC technology for crypto walletsNFC technology allows users to scan their devices to sign transactions, simplifying the process and enhancing security.
Zen Card is a prime example of a crypto wallet leveraging NFC technology. By integrating with the Coin98 Super Wallet, a mobile hot wallet, Zen Card allows users to create a hot wallet and securely transfer its data to the card via NFC. To execute a transaction, users simply scan their Zen Card with their phone, eliminating the cumbersome pairing or manual configuration processes typically associated with traditional cold wallets. This streamlined approach significantly improves user experience while maintaining a high level of security.
 Various crypto wallet products utilizing NFC technology.A selection of hardware wallets employing NFC technology.
Various crypto wallet products utilizing NFC technology.A selection of hardware wallets employing NFC technology.
Other notable NFC-enabled wallets include Tapsigner, Coldcard, Tangem, Keepser, and Sugi, each offering unique features and benefits. The growing adoption of NFC technology highlights its potential to become a standard feature in crypto wallets, facilitating secure and user-friendly transactions in the years to come.
Key Splitting: Enhanced Security for Private Keys
Key splitting, also known as cryptographic splitting, split-key encryption, or key sharding, is a vital security technique that divides a cryptographic key into multiple parts, storing and encrypting them in different locations. This process is particularly relevant for private keys, which are essential for accessing and managing crypto assets. The reconstruction of the original private key requires the combination of all or a specific number of these key parts, depending on the implementation.
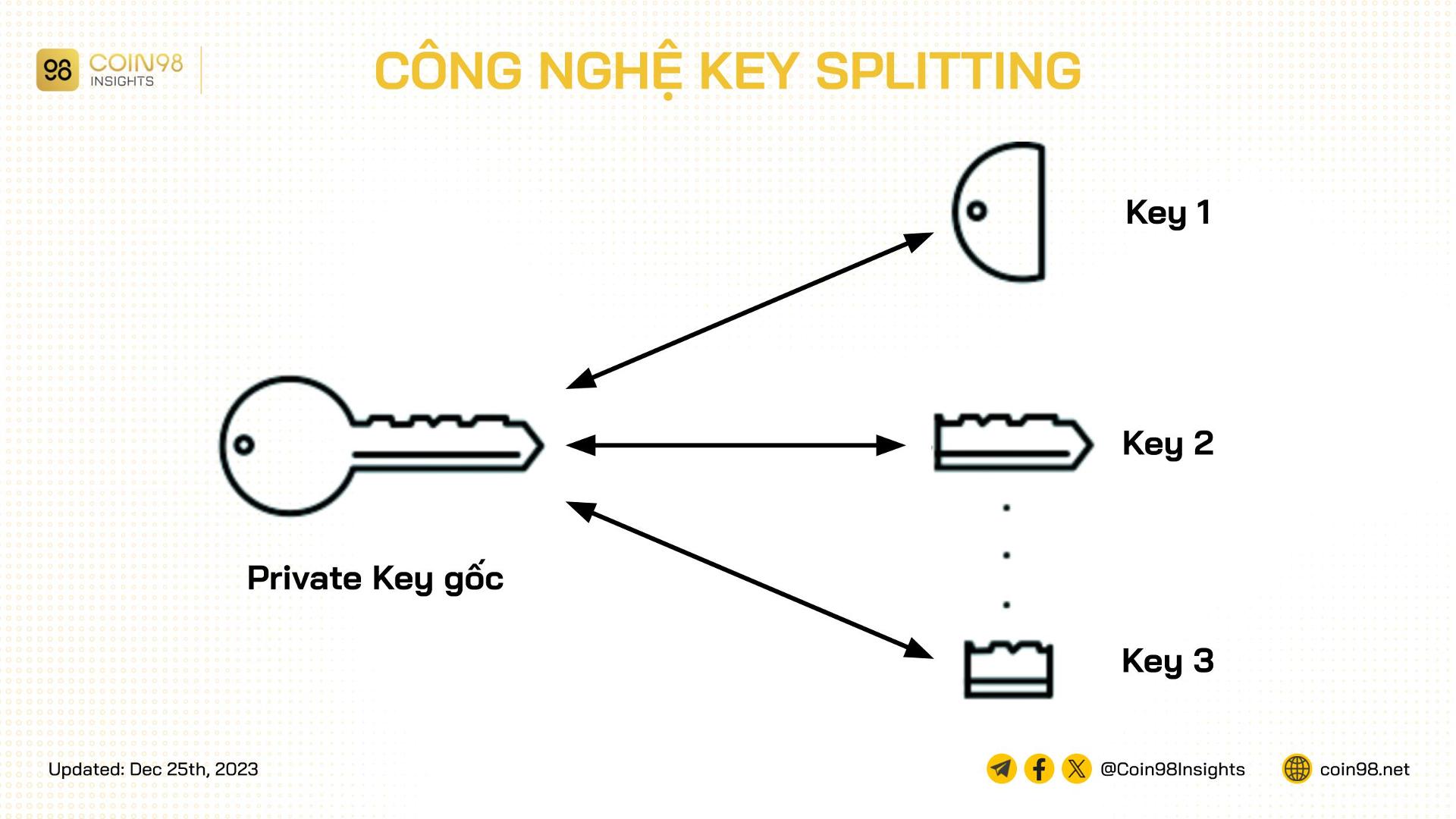 Key splitting technology divides private keys into multiple parts.Key splitting enhances security by dividing the private key into separate shards.
Key splitting technology divides private keys into multiple parts.Key splitting enhances security by dividing the private key into separate shards.
Key splitting significantly reduces the risk of key compromise. Even if one part of the key is exposed, the entire key remains secure as long as the other parts are protected. This added layer of security is particularly crucial in the crypto space, where private keys are often targeted by malicious actors.
Zen Card exemplifies the implementation of key splitting in a crypto wallet. By leveraging key splitting in conjunction with the Coin98 Super Wallet, the encrypted seed phrase or private key is split into two parts. One part is stored in the secure enclave of the user’s mobile phone, while the other resides on the Zen Card itself. To sign a transaction, both the card and the phone are required, ensuring that the complete key is never exposed in a single location. After the transaction is signed, the combined key is immediately discarded, further minimizing the risk of compromise.
 Zen Card utilizing key splitting technologyZen Card implements key splitting to bolster the security of user funds.
Zen Card utilizing key splitting technologyZen Card implements key splitting to bolster the security of user funds.
This decentralized key management approach enhances security and provides users with peace of mind. Even if one device is lost or compromised, the funds remain secure, as the attacker cannot reconstruct the full private key. Key splitting is becoming increasingly important for safeguarding digital assets in an increasingly interconnected world.
Account Abstraction: Personalized Account Management
Account abstraction (AA) is a proposed enhancement to Ethereum accounts that allows for the transformation of standard accounts into smart contracts with custom logic and conditions. This empowers users with granular control over their accounts, enabling them to define valid transactions, pay transaction fees, and initiate transactions according to their specific needs.
 Account abstraction allows users to customize their accounts with specific rules and logic.
Account abstraction allows users to customize their accounts with specific rules and logic.
AA essentially decouples the entity holding tokens (the account) from the entity authorizing transactions (the signer), paving the way for personalized account management. This flexibility allows for the creation of accounts tailored to individual requirements, whether it’s multi-signature security, social recovery options, or automated transaction processing.
Smart contract wallets, like Argent, Holdstation, Authereum, Avocado, Gnosis Safe, and Ambire Wallet, leverage account abstraction to offer enhanced security and user-friendliness. These wallets provide features such as multi-signature security, social recovery, address whitelisting/blacklisting, batched transactions, and account freezing, empowering users with greater control over their assets and transactions.
 Examples of smart contract walletsSmart contract wallets leverage account abstraction to offer advanced features and enhanced security.
Examples of smart contract walletsSmart contract wallets leverage account abstraction to offer advanced features and enhanced security.
Multisig: Enhancing Security through Shared Control
Multisig, short for multi-signature, requires two or more signatures to authorize a transaction, providing a higher level of security compared to single-signature transactions. Its most common application in the crypto world is in multi-signature wallets, which are owned by multiple entities and require the signatures of all or a majority of these entities to execute a transaction.
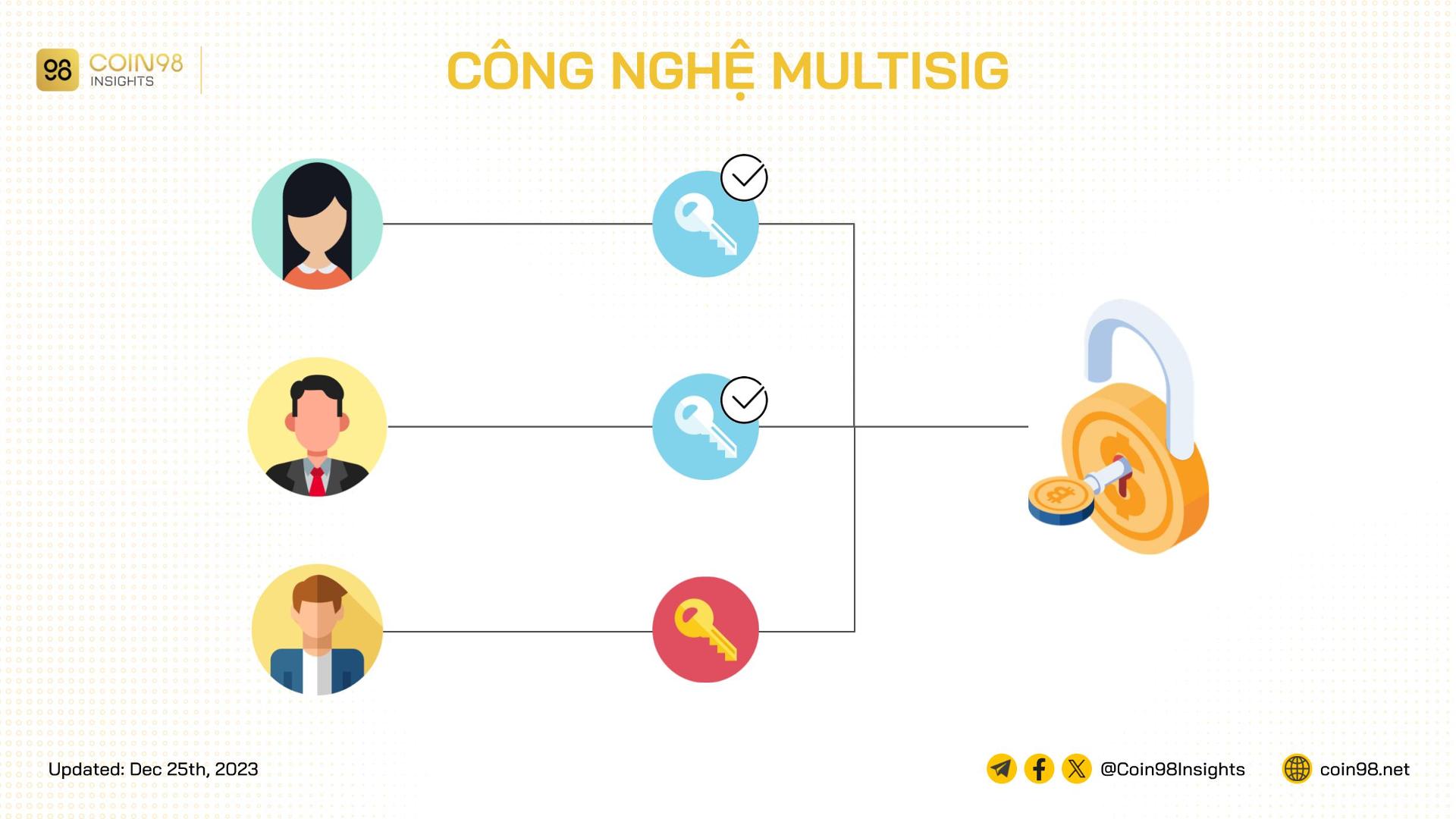 Multisig technology requires multiple signatures for transactionsMultisig wallets enhance security by requiring multiple signatures to authorize transactions.
Multisig technology requires multiple signatures for transactionsMultisig wallets enhance security by requiring multiple signatures to authorize transactions.
A multisig wallet can be visualized as a safe deposit box with multiple locks and keys. Each authorized entity holds a key, and only when the required number of keys are used simultaneously can the box be opened. This shared control mechanism prevents any single entity from unilaterally accessing or controlling the funds.
Multisig wallets are often designated as M-of-N wallets, where M represents the minimum number of signatures required for a transaction, and N represents the total number of authorized signatures. Common configurations include 2-of-3, 3-of-5, or even more complex setups. DAOs (Decentralized Autonomous Organizations) frequently utilize multisig wallets to manage treasury funds, ensuring that decisions are made collectively and transparently. This prevents any single individual or small group from misusing or misappropriating the organization’s assets.
Social Login: Bridging Web2 and Web3
Social login allows users to access applications using their existing social media accounts, such as Facebook, Google, or X (formerly Twitter). This streamlined login process simplifies user onboarding and eliminates the need for creating and remembering multiple usernames and passwords.
 Social login for crypto walletsSocial login simplifies access to crypto wallets by leveraging existing social media accounts.
Social login for crypto walletsSocial login simplifies access to crypto wallets by leveraging existing social media accounts.
Social login plays a significant role in bridging the gap between Web2 and Web3. It allows Web2 users to seamlessly transition into the Web3 space without the complexities of traditional wallet creation and management. This simplified approach addresses the challenges faced by new users who may be intimidated by the technical aspects of private keys and seed phrases.
Crypto wallets like Coin98 Super Wallet, Ramper Wallet, Pulse Wallet, and Torus Wallet have integrated social login functionality, making it easier for users to create and access their wallets. Ramper Wallet, in particular, allows users to create and access their wallets via Facebook, Email, or Apple ID, offering a user-friendly experience while maintaining robust security.
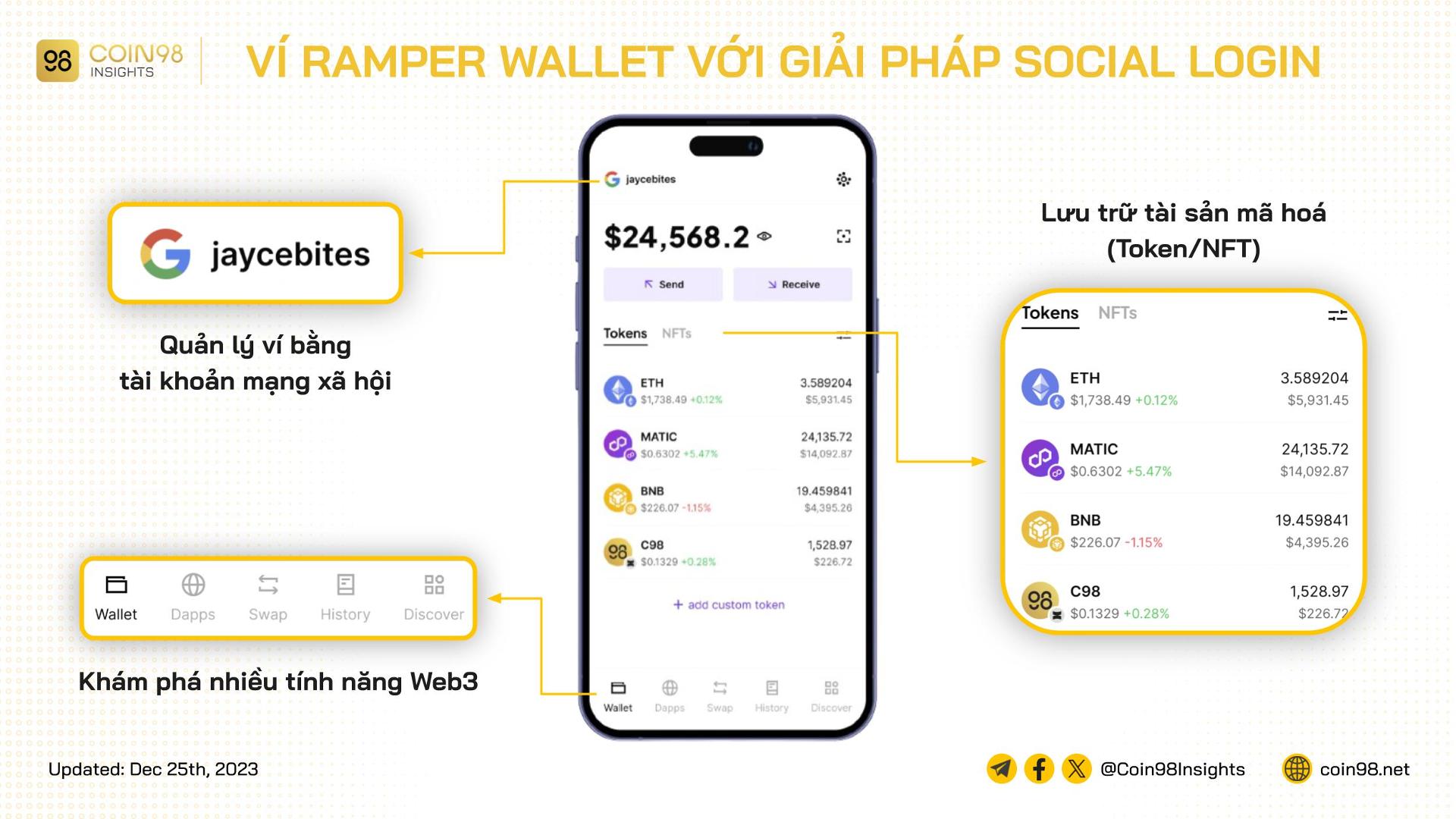 Ramper Wallet utilizing social loginRamper Wallet exemplifies the use of social login in a crypto wallet, simplifying access for Web2 users.
Ramper Wallet utilizing social loginRamper Wallet exemplifies the use of social login in a crypto wallet, simplifying access for Web2 users.
By focusing on simplicity and user-friendliness, social login empowers a wider audience to participate in the Web3 ecosystem, accelerating mass adoption and driving the evolution of the decentralized web.
Conclusion: The Future of Crypto Wallets
The technologies discussed above – NFC, Key Splitting, Account Abstraction, Multisig, and Social Login – represent key advancements in the crypto wallet landscape. They are shaping the future of digital asset management by focusing on enhanced security, improved user experience, and increased accessibility. As the crypto ecosystem continues to mature, these technologies will play a critical role in driving mainstream adoption and empowering users with greater control over their digital assets.
FAQ: Addressing Common Queries about Crypto Wallet Technologies
Q: What are the primary benefits of using an NFC-enabled crypto wallet?
A: NFC wallets offer enhanced security by storing private keys offline, along with improved convenience through contactless transactions, eliminating the need for cables or complex setup procedures.
Q: How does key splitting improve the security of my crypto assets?
A: Key splitting divides your private key into multiple parts, making it significantly more difficult for attackers to compromise your funds, even if one part of the key is exposed.
Q: What are the advantages of account abstraction in smart contract wallets?
A: Account abstraction allows for customizable account logic, enabling features like multi-signature security, social recovery, and automated transactions, offering greater control and flexibility for users.
Q: How do multisig wallets enhance security for DAOs and other organizations?
A: Multisig wallets require multiple signatures to authorize transactions, preventing any single individual from controlling funds and promoting transparency and shared governance.
Q: Why is social login important for the adoption of Web3 applications?
A: Social login simplifies the onboarding process for new users by allowing them to access Web3 applications using their existing social media accounts, removing a significant barrier to entry and accelerating mass adoption.
We encourage you to share this article and ask any further questions you may have about these transformative crypto wallet technologies. Your engagement helps us to better understand the needs of the community and to continue providing valuable insights into the evolving world of digital assets.